
If you were buying a manufacturing plant, you wouldn't just look at the P&L. You would walk the factory floor. You would check if the machinery was rusted, if the safety protocols were followed, and if the building was up to code.
Yet, in software M&A, smart investors routinely buy "black boxes." They stare at EBITDA bridges and customer retention charts, assuming the product underneath is sound. The reality? You are likely buying a lemon. According to the 2024 Synopsys Open Source Security and Risk Analysis Report, 74% of commercial codebases contain high-risk vulnerabilities—a massive 54% surge from just two years prior.
This isn't just a "technical nuance." It is financial poison. When you acquire code riddled with architectural rot or licensing violations, you are inheriting a massive CapEx bill that isn't in your deal model. We call this Hidden Remediation Capex. It surfaces 90 days post-close, usually when you try to integrate a new feature or scale the platform, and the engineering team tells you, "We can't. We have to rewrite the core first."
Suddenly, your 100-day value creation plan is dead on arrival. Instead of shipping new features to drive cross-sell, you are spending the next 12 months paying down someone else's debt. You need a way to assess the "factory floor" quickly, without slowing down the deal velocity. You need the 5-Day Code Audit.
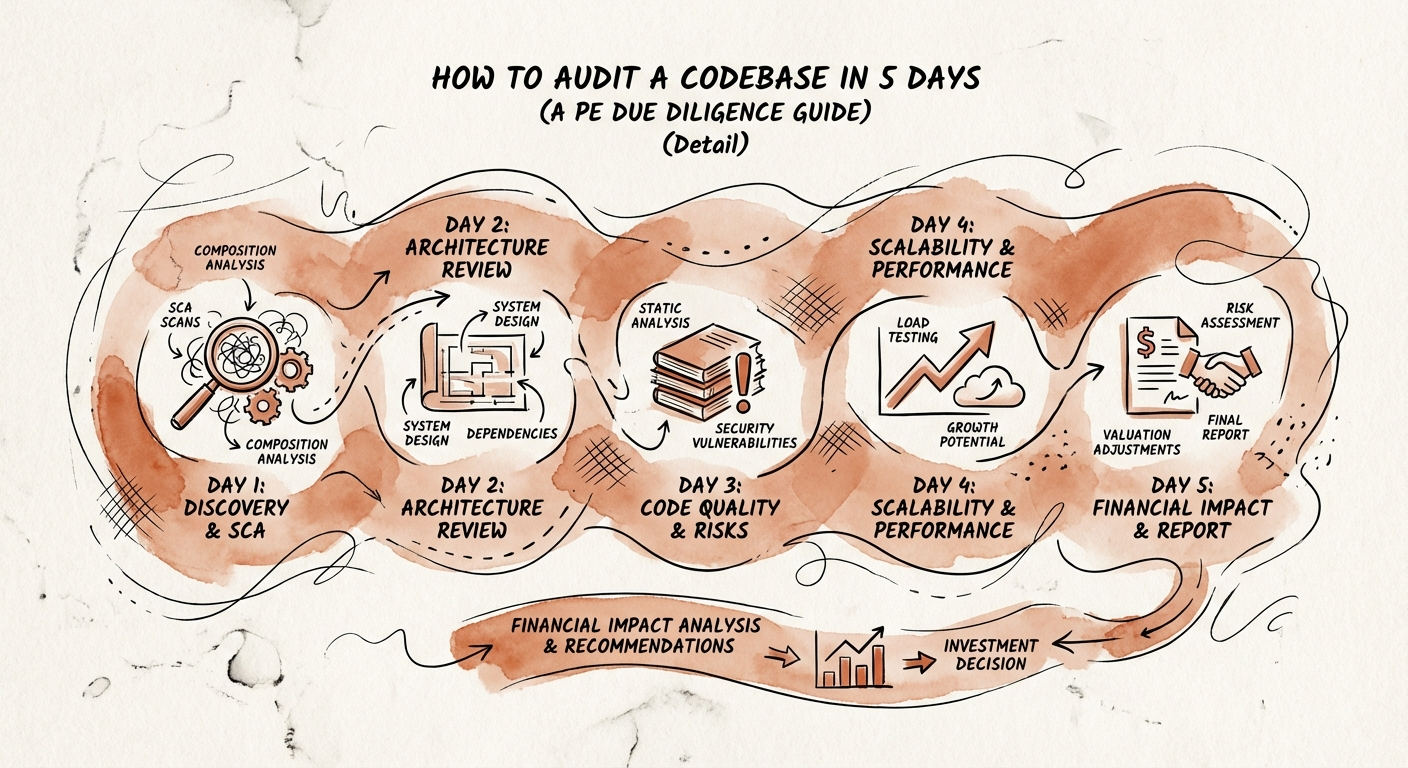
You do not need a three-month research project. You need a targeted, operator-led assessment that focuses on Red Flags and Remediation Costs. Here is the exact schedule we use for rapid technical due diligence.
Before interviewing a single engineer, we run automated scans. We use Software Composition Analysis (SCA) tools to scan the codebase for two things: high-severity vulnerabilities (CVEs) and toxic open-source licenses (like GPL). Finding a GPL component in a proprietary commercial product is a potential deal-killer—it could force you to open-source your entire IP. Skipping this step is a $2M mistake waiting to happen.
We look at the database schema and the system topology. Is this a "distributed monolith" masquerading as microservices? Are there single points of failure? We often find that 80% of the logic is trapped in a 10-year-old legacy database that cannot scale past the next 5,000 users. If your thesis relies on "platform scaling," this finding requires an immediate purchase price adjustment to cover the re-platforming costs.
Code quality matters, but shipping velocity matters more for value creation. We audit the team's ability to release software. We look at Deployment Frequency and Lead Time for Changes. If the team releases once a quarter, they are not agile; they are terrified. This indicates brittle code that breaks whenever it is touched.
We analyze the AWS/Azure bill. Usually, we find 20-30% waste—dev environments running 24/7, unattached storage volumes, and over-provisioned instances. This is effectively "free EBITDA" you can capture post-close, but only if you identify it now. Conversely, we check for "security debt"—open S3 buckets or unencrypted databases that could lead to a breach.
We do not deliver a 100-page academic paper. We deliver a one-page financial summary: "To achieve the growth targets in the CIM, you must spend $1.5M in Year 1 on technical remediation." This is the number you take back to the investment committee.
The goal of this audit is not to kill the deal (unless we find fatal IP issues). The goal is to price the risk accurately. If our audit reveals that the target requires a $3M architectural rewrite to be compliant with your security standards, that is $3M of working capital that needs to be accounted for.
Use the "Remediation Roadmap" to adjust the multiple. We have seen firms successfully lower the purchase price by the exact amount of the estimated technical debt remediation. This isn't nitpicking; it's quantifying technical debt as a financial liability.
Ultimately, software due diligence is about risk mitigation. You are buying the future cash flows of a technology asset. If that asset is rusting from the inside out, you need to know before the wire transfer clears. Don't buy the brochure. Audit the engine.
