
For the Enterprise CIO or VP of Engineering in the mid-market, the world just got significantly more expensive. If you are operating in the Defense Industrial Base (DIB), healthcare, or critical infrastructure, the mandate has shifted from "reasonable security" to "defense-grade assurance." The arrival of CMMC 2.0 (Cybersecurity Maturity Model Certification) has turned what was once a paperwork exercise into a binary survival metric: get certified or lose the contract.
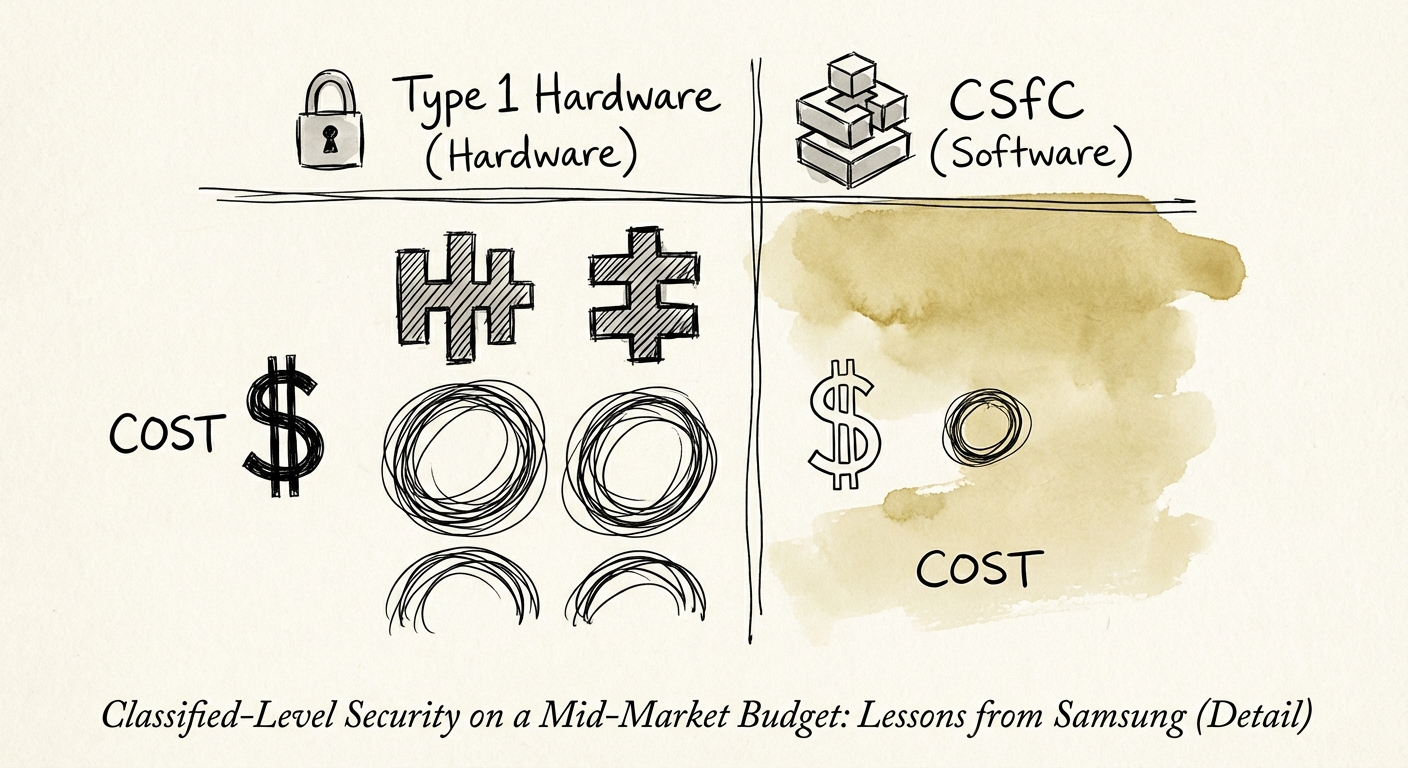
The problem is the math. Traditional "Classified" security—the kind used by the NSA and DoD—was historically built on Type 1 encryption. These are bespoke, proprietary hardware devices, physically hardened, astronomically expensive, and requiring specialized handlers. For a Fortune 100 contractor like Lockheed Martin, buying $5,000 encrypted hard drives and maintaining SCIFs (Sensitive Compartmented Information Facilities) is a rounding error. for a mid-market firm with $50M in revenue, it is EBITDA suicide.
You are likely facing a "Transition Tom" scenario: A major digital transformation or new market entry is stalled because your security architecture cannot satisfy a governance committee or a prime contractor’s flow-down requirements. You are stuck between a board that refuses to double your IT budget and a Compliance Officer who refuses to sign off on the risk.
The way out isn't to buy more expensive hardware. It's to change the architecture entirely. The precedent for this shift comes from an unlikely source: a consumer electronics giant that convinced the NSA to let commercial smartphones handle classified data.
In 2014, a quiet revolution occurred in government security. The NSA approved Samsung Knox-enabled devices for use under the Commercial Solutions for Classified (CSfC) program. This was a paradigm shift. For decades, "classified" meant "custom." Suddenly, the NSA admitted that mass-produced, commercial-off-the-shelf (COTS) hardware—if properly architected—could be trusted with the nation's secrets.
The lesson for the mid-market CIO is not to go buy 500 Samsung phones. The lesson is how Samsung achieved the certification. They didn't build a thicker phone; they built a smarter stack. The CSfC framework replaces the "unbreakable box" (Type 1) with the "redundant layers" principle.
To achieve classified handling on a commercial budget, you must adopt two core CSfC rules:
We call the cost of security deadlock the 53% Tax—the hidden operational drag of stalled projects. By adopting a CSfC-style approach (Software-Defined Security on commodity hardware), you bypass the need for proprietary hardware.
Consider the benchmarks. Achieving CMMC Level 2 compliance involves 110 controls from NIST SP 800-171. Recent data places the cost for a mid-sized firm (50-250 employees) between $175,000 and $233,000 for initial preparation and assessment. If you attempt to meet these controls using legacy "Type 1" thinking—dedicated circuits, air-gapped hardware, and proprietary encryption appliances—that cost can easily triple.
Modern cybersecurity risks aren't mitigated by spending more; they are mitigated by architecting better. Samsung proved that a $800 device, when wrapped in the right policy and software (Knox Platform for Enterprise), is more secure than a $5,000 legacy encryptor that hasn't been patched in three years.
If your digital transformation is stuck in committee due to security concerns, or if you are staring down a CMMC audit with a terrified wallet, execute this three-step pivot.
Audit your current security spend. Identify every line item that is "proprietary security hardware." If you are paying for dedicated encryption bridges or legacy VPN concentrators, mark them for replacement. Your goal is to move to software-defined perimeters (SDP) and Zero Trust Network Access (ZTNA) that run on commodity servers or cloud infrastructure. Metric to watch: Reduction in hardware maintenance contracts.
For your most sensitive data (CUI or IP), implement the CSfC "tunneled" approach. Do not trust the transport. Use application-layer encryption on top of network-layer encryption. For mobile fleets, enforce the "Dual-DAR" (Dual Data-at-Rest) standard found in modern MDM profiles. This satisfies the "Defense in Depth" requirement of CMMC without requiring you to issue James Bond gadgets to your sales team.
The Samsung approval wasn't just about the chip; it was about the Protection Profile (MDFPP). You must document your configuration management. Most mid-market firms fail audits not because they lack security, but because they lack proof of security. Automate your compliance reporting. If you can't prove the configuration state of an endpoint in real-time, it is not secure.
The days of security through obscurity are over. The days of security through infinite budget are gone. The winning strategy for the mid-market CIO is Security through Standardization. By adopting the architectural lessons of the CSfC program—layering commercial technologies to achieve classified results—you don't just pass the audit. You unlock the agility your business needs to scale.
